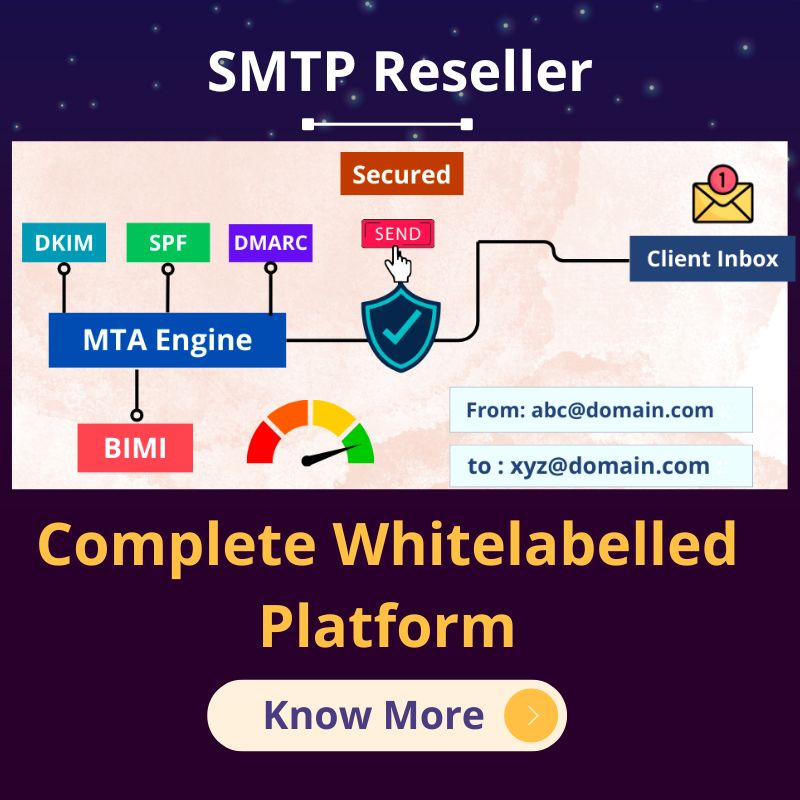
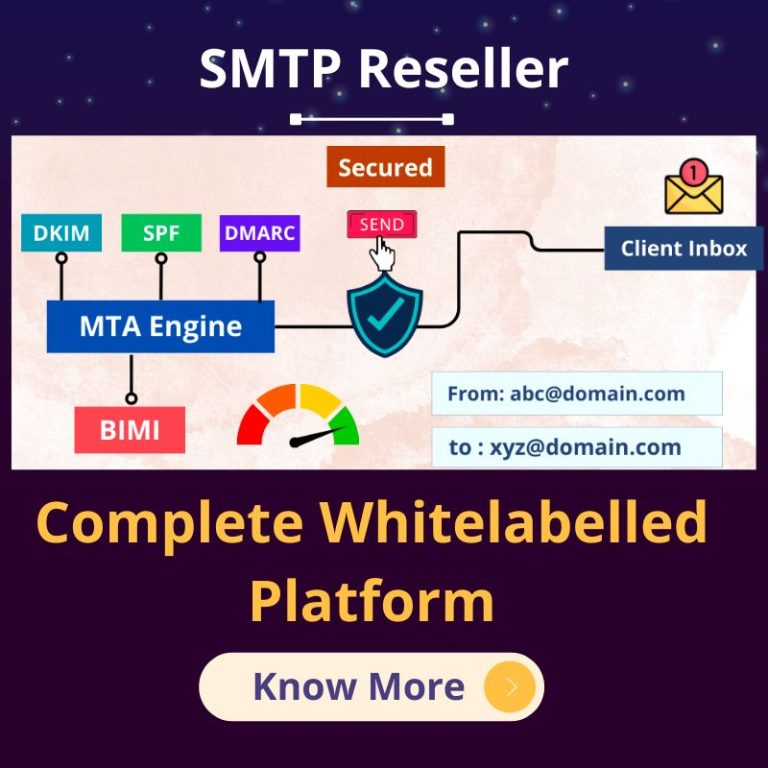
MigoSMTP is the Best SMTP Server Provider in India
An SMTP server is the most reliable email server when it comes to sending out emails to clients and customers. MigoSMTP provides cost-efficient Simple Mail Transfer Protocol (SMTP) for a standard communication protocol for sending email messages on business networks and the Internet.
As most businesses are going online, the need for email marketing is increasing by the day. Most e-mail systems that send mail over the Internet use SMTP to send messages from one server to another. The main purpose of SMTP is to deliver messages to user’s mailboxes.
How Does SMTP Server Works?
All modern email client programs support SMTP. The SMTP settings maintained in an email client include the IP address of an SMTP server (along with the addresses of either a POP or IMAP server for receiving emails). Web-based clients embed the address of an SMTP server inside their configuration, while PC clients provide SMTP settings that allow users to specify their own server of choice.
A physical SMTP server may be dedicated to servicing email traffic only but is often combined with at least POP3 and sometimes other proxy server functions.
SMTP runs on top of TCP/IP and uses TCP port number 25 for standard communication. To improve SMTP and help combat spam on the Internet, standards groups have also designed TCP port 587 to support certain aspects of the protocol. A few Web email services, such as Gmail, use the unofficial TCP port 465 for SMTP. Related: Key Features of SMTP Server
Why MigoSMTP is the Best SMTP Server Provider in India
Our Transactional SMTP Server reliable sending platform delivers your transactional messages to the inbox and scales with your volume needs.
MigoSMTP SMTP Server is a top-grade SMTP relay service that easily integrates with various email marketing applications and helps you maximize email rate rates. MigoSMTP is the Best SMTP Server Provider in India offers many affordable plans which are extremely affordable and are loaded with many advanced and future features. Which you can send thousands of emails at a fast pace.
The MigoSMTP SMTP server can be used to send emails for a variety of purposes and the option of early customer support can be taken for further assistance.
Features of MigoSMTP
- Inbox Delivery:- With this SMTP service, you are 99% inbox delivery due to its white servers. MigoSMTP gives priority to Inbox delivery of SMTP email.
- Multiple Domains:- MigoSMTP SMTP supports multiple domains, which means that you can send emails through different domains and addresses using the same account.
- DKIM Server:- The SMTP service embeds a DKIM signature to get a higher delivery rate and also sends emails to customers at a higher speed.
Pricing
The MigoSMTP Best SMTP Server Provider in India has got several pricing plans which are very cost effective as well as full of different features.
- Take advantage of the free price plan of service, and send a newsletter to a small mailing list.
- A transition from one value plan to another can be done by the customer at any time.
- Delivery of letters around the world and professional online technical support are both attractive features of each of the current plans.
- Our Nuclear SMTP server is available to customers anywhere on the planet.
Benefits
1. A Complete Analysis of Sent Emails
Whether an email is received, delayed, not sent or bounces back, you will know right away and you will know why. You have a way of knowing for sure if it was received through reports with your own SMTP server.
2. Email Privacy with Your Full Control
Your lists are secure in your hands, and not vulnerable in anybody else’s. You can use your lists in the best way that engages your customers. You can segment and combine lists in any way you want for testing and campaigns.
3. No Restriction by Third Party ToCs
You will not be held back by restrictions imposed by third parties who also have to work with other clients. The actions of other third-party clients could affect your own deliverability. Because you will be sharing servers, your email deliverability is also compromised if they do anything spammy.
4. Cost Efficient
In terms of time and dollars spent, the investment for running your own server may be a little heavy at the onset because of time invested in learning and setting up – but it gets easy. Once set, you will not need to pay a monthly service fee or pay per email sent like you would with 3rd parties.
5. Sharing
When you are using other providers, they always share servers, share IPs and share staff. Unless you send millions of emails every day, you end up sharing your server with 200 or more other marketers. If anyone of them gets blocked – you will also be blocked, so through no fault of your own, you may be labeled a spammer and your emails could be declined until the provider takes action.
6. Tracking Emails and Maintaining Reports
In an email marketing strategy, it is very important to track the status of your emails. Tracking your emails is only possible if you use a Best SMTP Server in India. Your emails will be tracked until they are delivered to the recipient. You can also find out whether your mail has bounced, is in the queue or has been deferred. It is also possible to find out the recipients reaction and response to the email. Using this service, you can now find out how successful your email marketing strategy has been.
7. Avoids Emails from Going into SPAM
What happens most of the times is that your email or newsletter goes into spam or the junk mail of the recipient. This way, many emails do not reach recipients inbox and are therefore deleted even before it is opened. Best SMTP Server Provider in India make sure that your emails reach the inbox of the recipients without fail. This reliable service helps people circulate their emails and newsletters without the fear of them landing up in the junk mail or as spam.
Summary!
There is various Best SMTP Server provider available in the market but I would like to recommend MigoSMTP SMTP Services as we have personally used and verified its features.
I can assure you that MigoSMTP SMTP Services is the cheapest among all and offer a higher delivery rate for sending emails.